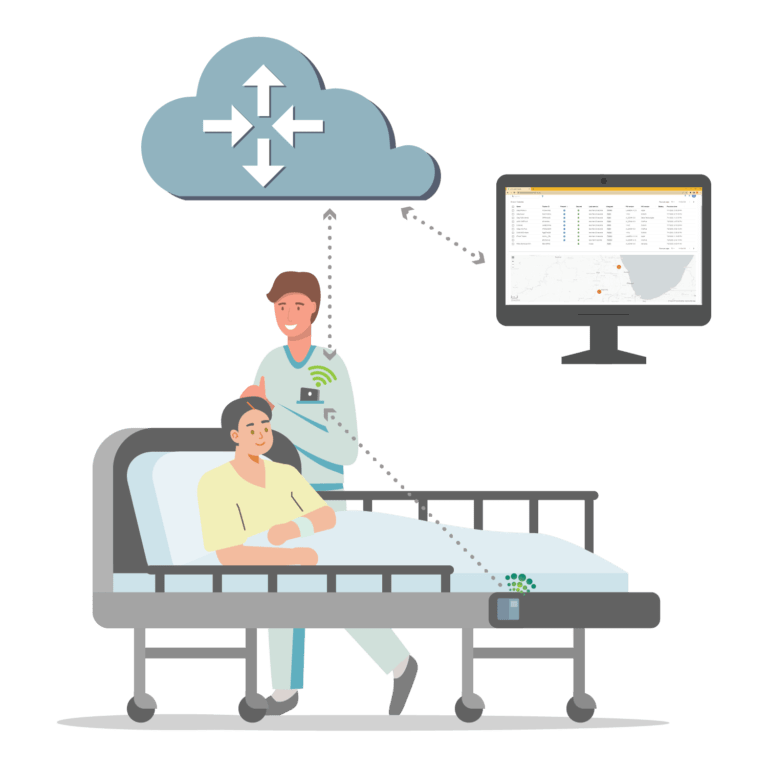
A secure pervasive IoT solution
The expense of patched and fragmented IoT deployments is more than simply cost, it’s security. An out-of-the-box solution now exists that offers a single, secure data tunnel for pervasive IoT enabling efficient and secure asset tracking, inventory management, logistics, and compliance applications.
With Luna, an integrator can quickly create a shared, seamless Bluetooth Low Energy (BLE) network of interconnected devices that give telemetry and location data anywhere, conveniently and securely. Because security is built as a core component of the Luna protocol, the solution holds up even when it meets the existing infrastructure of an organization’s communication systems.
Luna is a BLE-to-cloud communications protocol that deploys on new or existing devices and hardware infrastructure. Secure data gathering becomes a reality for barcode scanner / mobile computer tracking, asset tracking, and real-time visibility in supply-chain and healthcare industries.
Secure communication through ubiquitous gateways
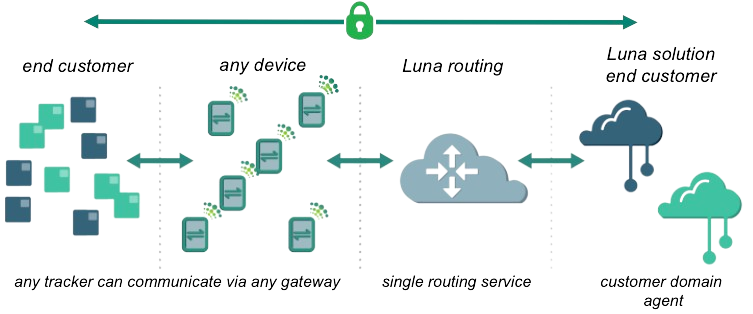
Traditionally, to ensure secure communication, each IoT application required its own dedicated IoT gateway components and each required its own unique gateway infrastructure. Today, Luna simplifies IoT deployment while maintaining security by implementing neutral gateways. The gateways neither see nor hold the data but rather they forward encrypted packets to a routing service without being privy to any content, where the data comes from, where it will eventually reside, or who it belongs to.
The Luna network is a secure tunnel that transports data between BLE IoT devices and an IoT solution provider’s back-end application or cloud. Existing devices such as barcode readers, scanners, workers’ cell phones, or printers act as neutral gateways when enabled by Luna SDK. This means BLE devices have more pathways to reach the cloud in the high-level secure environment enabled by the Luna protocol.
End-to-end communication security — no snooping or spoofing
In a traditional BLE solution, security exists only between a device and a gateway. In that configuration, the gateway must be a trusted party. Improving on the tradition, Luna’s end to end security extends encryption and verification from the device all the way to the customer cloud. No intermediate systems, including gateways, need be trusted. In the Luna solution, gateways are zero trust entities. Trust is established at the end points: between the IoT device in the field and the customer’s cloud. Luna provides both open standards based communication and device interoperability without compromising security.
Luna’s encryption system is founded on approved industry standards, with 128 bit Elliptic Curve Diffie Hellman (ECDH) key exchange between device and cloud, and Authenticated Encryption (AE) using the Advanced Encryption Standard (AES) for message exchange.

Device and location privacy
IoT security needs to go beyond end-to-end communication encryption to prevent device tracking and spoofing. Luna enabled devices emit time-varying identifiers (ephemeral identifiers), which change apparently randomly every few minutes, but are completely predictable only by the Luna agent. These identifiers are generated using SHA 256 hash computations on ECDH generated encryption keys. Location information appended by the gateway is one-time encrypted using these ephemeral identifiers to eliminate all identifiable information from device notifications.
Cloud hosting options for tailored privacy
The Luna agent, which is the data encryption center, can be hosted by the end user, by the solution provider, or by Luna (see figure). When the user hosts the agent, the data is fully controlled by the end user and no other entity can access that data. This configuration is especially useful for military or health-agency end users where data access is highly restricted. Other end users whose data is not as restricted might choose that their data encryption be managed by the solution provider or by Luna.
Ready for secure growth
Luna’s strong security frees IoT solution providers to use their expertise to innovate on top of the network rather than to spend time building it. Luna’s secure and open network architecture simplifies adding new devices and can be deployed on a wide range of hardware securely.

Schedule a consultation to learn how Luna can help you enhance your visibility and operations.